What Command Below Must Be Used to Tell Wsus to Utilize Ssl?
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Windows Server Update Services all-time practices
This article provides tips for avoiding configurations that experience poor functioning because of design or configuration limitations in WSUS.
Original product version: Configuration Manager (current branch), Windows Server Update Services
Original KB number: 4490414
Chapters limits
Although WSUS can back up 100,000 clients per server (150,000 clients when you use Configuration Managing director), nosotros don't recommend budgeted this limit.
Instead, consider using a configuration of 2-iv servers sharing the same SQL Server database. This way y'all have rubber in numbers. If i server goes down, it won't immediately spoil your weekend because no client tin update while y'all must be updated against the latest zippo-twenty-four hour period exploit.
The shared database scenario too prevents a scan tempest.
A scan storm can occur when many clients change WSUS servers and the servers don't share a database. WSUS tracks activeness in the database, so that both know what has changed since a customer terminal scanned and will only send metadata that'due south updated since and so.
If clients change to a different WSUS server that uses a different database, they must do a full scan. A full scan tin cause large metadata transfers. Transfers of greater than 1 GB per customer may occur in these scenarios, especially if the WSUS server isn't maintained correctly. It tin can generate enough load to cause errors when clients communicate with a WSUS instance. And clients retry repeatedly in this instance.
Sharing a database means when a client switches to another WSUS instance that uses the same DB, the scan penalty isn't incurred. The load increases aren't the big penalization you pay for switching databases.
Configuration Manager client scans put more than need on WSUS than the stand-alone Automatic Updates. Configuration Managing director, because information technology includes compliance checking, requests scans with criteria that will return all updates that are in any status except declined.
When the Automatic Updates Agent scans, or you select Cheque for Updates in Command Panel, the agent sends criteria to recollect only those updates Approved for Install. The metadata returned will usually exist less than when the scan is initiated by Configuration Director. The Update Amanuensis does cache the data, and the next browse requests will render the information from the client cache.
Disable recycling and configure memory limits
WSUS implements an internal enshroud that retrieves the update metadata from the database. This performance is expensive and very memory intensive. It can cause the IIS application pool that hosts WSUS (known every bit WSUSPool) to recycle when WSUSPool overruns the default private and virtual memory limits.
When the pool recycles, the cache is removed and must be rebuilt. Information technology isn't a large problem when clients are undergoing delta scans. But if you stop upward in a scan tempest scenario, the pool volition recycle constantly. And clients volition receive errors when you lot make scan requests, such as HTTP 503 errors.
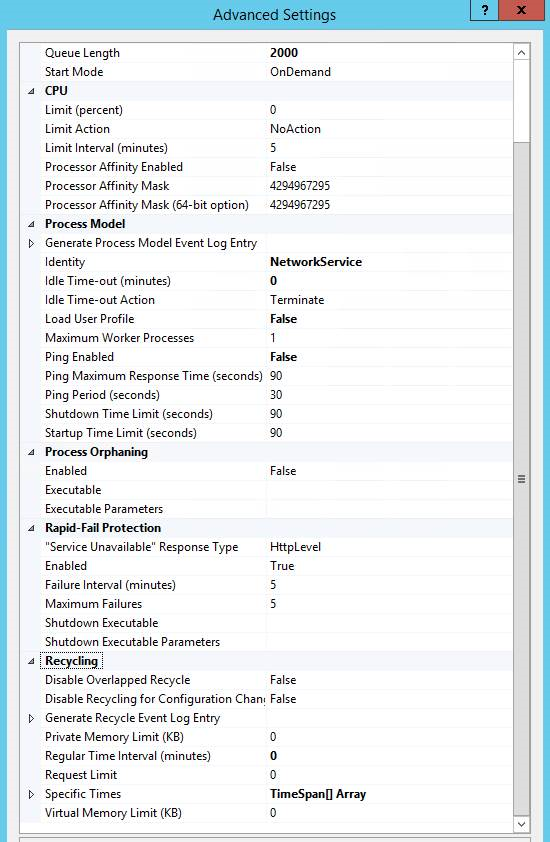
We recommend that you increase the default Queue Length, and disable both the Virtual and Private Retentivity Limit past setting them to 0. IIS implements an automatic recycling of the application pool every 29 hours, Ping, and Idle Fourth dimension-outs, all which should be disabled. These settings are found in IIS Manager > Awarding Pools > cull WsusPool and so click the Advanced Settings link in the right side pane of IIS manager.
Here's a summary of recommended changes, and a related screenshot. For more information, see Plan for software updates in Configuration Managing director.
| Setting proper noun | Value |
|---|---|
| Queue Length | 2000 (up from default of yard) |
| Idle Time-out (minutes) | 0 (down from the default of xx) |
| Ping Enabled | Simulated (from default of True) |
| Private Retention Limit (KB) | 0 (unlimited, up from the default of 1,843,200 KB) |
| Regular Time Interval (minutes) | 0 (to prevent a recycle, and modified from the default of 1740) |
In an environment that has around 17,000 updates cached, more than than 24 GB of memory may be needed as the cache is built until it stabilizes (at around fourteen GB).
Check whether compression is enabled (if you lot want to conserve bandwidth)
WSUS uses a compression type calls Xpress encoding. It implements compression on update metadata, and can result in significant bandwidth savings.
Xpress encoding is enabled in IIS ApplicationHost.config with this line under the <httpCompression> chemical element and a registry setting:
-
ApplicationHost.Config
<scheme proper name="xpress" doStaticCompression="fake" doDynamicCompression="truthful" dll="C:\Program Files\Update Services\WebServices\suscomp.dll" staticCompressionLevel="10" dynamicCompressionLevel="0" />
-
Registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Update Services\Server\Setup\IIsDynamicCompression
If both aren't present, it can be enabled by running this command and so restarting the WsusPool application pool in IIS.
cscript "%programfiles%\update services\setup\DynamicCompression.vbs" /enable "%programfiles%\Update Services\WebServices\suscomp.dll" Xpress encoding will add together some CPU overhead, and can be disabled if bandwidth isn't a concern, but CPU usage is. The following command will plough it off.
cscript "%programfiles%\update services\setup\DynamicCompression.vbs" /disable Configure products and categories
When you configure WSUS, choose merely the products and categories that yous plan to deploy. You can always synchronize categories and products that you must accept later on. Adding them when you don't plan to deploy them increases metadata size and overhead on the WSUS servers.
Disable Itanium updates and other unnecessary updates
It shouldn't be an issue for much longer, because Windows Server 2008 R2 was the last version to support Itanium. Merely it bears mentioning.
Customize and employ this script in your environment to decline Itanium architecture updates. The script can also decline updates that contain Preview or Beta in the update title.
It leads to the WSUS console being more responsive, but doesn't touch the client scan.
Turn down superseded updates and run maintenance
One of the virtually of import things that you can do to assist WSUS run better. Keeping updates around that are superseded longer than needed (for example, after you're no longer deploying them) is the leading crusade of WSUS functioning problems. It'due south ok to keep them effectually if y'all're still deploying them. Remove them after yous're done with them.
For information nigh declining superseded updates and other WSUS maintenance items, come across the Complete guide to Microsoft WSUS and Configuration Manager SUP maintenance commodity.
WSUS with SSL setup
By default, WSUS isn't configured to use SSL for client communication. The get-go mail-install step should be to configured SSL on WSUS to brand sure security betwixt server-client communications.
Y'all must have one the following actions:
- Create a self-signed certificate. It isn't ideal considering every client would have to trust this certificate.
- Obtain one from a third-party certificate provider.
- Obtain one from your internal certificate infrastructure.
Your document must have the brusque server name, FQDN, and SAN names (aliases) that it goes by.
After you have the document installed, upgrade the Grouping Policy (or Client Configuration settings for software updates in Configuration Manager) to use the address and SSL port of the WSUS server. The port is typically 8531 or 443.
For example, configure GPO Specify intranet Microsoft update service location to <https://wsus.contoso.com:8531>.
To get started, run across Secure WSUS with the Secure Sockets Layer Protocol.
Configure Antivirus Exclusions
- Antivirus scans
- Microsoft Anti-Virus Exclusion List
Nearly Cumulative Updates and Monthly Rollups
Y'all may see the terms Monthly Rollups and Cumulative Update used for Windows Os updates. They may exist used interchangeably. Rollups refer to the updates published for Windows 7, Windows 8.i, Windows Server 2008 R2, and Windows Server 2012 R2 that are only partly cumulative.
For more information, come across the following blog posts:
- Simplified servicing for Windows 7 and Windows viii.i: the latest improvements
- More on Windows 7 and Windows 8.1 servicing changes
With Windows ten and Windows Server 2016, the updates were cumulative from the beginning:
- Windows 10 update servicing cadence
Cumulative means that: you install the release version of the OS, and only have to use the latest Cumulative Update to be fully patched. For the older operating systems, we don't accept such updates yet, although it's the direction we're heading in.
For Windows 7 and Windows 8.ane, information technology means that afterwards you install the latest monthly rollup, more updates volition still be needed. Hither's an case for Windows 7 and Windows Server 2008 R2 on what it takes to have an almost fully patched arrangement.
The following table contains the list of Windows Monthly Rollups and Cumulative Updates. Yous tin as well notice them by searching for Windows <version> update History.
| Windows version | Update |
|---|---|
| Windows seven SP1 and Windows Server 2008 R2 SP1 | Windows 7 SP1 and Windows Server 2008 R2 SP1 update history |
| Windows 8.1 and Windows Server 2012 R2 | Windows viii.1 and Windows Server 2012 R2 update history |
| Windows 10 and Windows Server 2016 | Windows 10 and Windows Server update history |
| Windows Server 2019 | Windows 10 and Windows Server 2019 update history |
Some other betoken to consider is that not all updates are published so that they sync automatically to WSUS. For instance, C and D week Cumulative Updates are preview updates and won't synchronize to WSUS, but must exist manually imported instead. See the Monthly quality updates section of Windows 10 update servicing cadence.
Using PowerShell to connect to a WSUS server
Hither'southward simply a lawmaking example to get y'all started with PowerShell and the WSUS API. Information technology can be executed where the WSUS Administration Console is installed.
[void][reflection.assembly]::LoadWithPartialName("Microsoft.UpdateServices.Assistants") $WSUSServer = 'WSUS' # This is your WSUS Server Name $Port = 8530 # This is 8531 when SSL is enabled $UseSSL = $False #This is $True when SSL is enabled Try { $Wsus = [Microsoft.UpdateServices.Administration.AdminProxy]::GetUpdateServer($WSUSServer,$UseSSL,$Port) } Catch { Write-Alert "$($WSUSServer)<$($Port)>: $($_)" Pause } References
-
SUS Web log
-
WSUS Production Squad Web log
-
The complete guide to Microsoft WSUS and Configuration Manager SUP maintenance
-
How does Windows Update work?
-
Introduction to WSUS and PowerShell
-
Use PowerShell to Perform Basic Administrative Tasks on WSUS
-
Approve or Turn down WSUS Updates past Using PowerShell
-
Use PowerShell to Find Missing Updates on WSUS Customer Computers
-
Get Windows Update Status Information by Using PowerShell
-
Introduction to PoshWSUS, a Gratis PowerShell Module to Manage WSUS
-
Use the Free PoshWSUS PowerShell Module for WSUS Authoritative Work
-
Download resources and applications for Windows, SharePoint, Part, and other products
-
PowerShell UI used for auditing and installing updates from WSUS to local and remote systems
-
PowerShell module to manage Windows Server Update Services (WSUS)
Source: https://docs.microsoft.com/en-us/troubleshoot/mem/configmgr/windows-server-update-services-best-practices
0 Response to "What Command Below Must Be Used to Tell Wsus to Utilize Ssl?"
Post a Comment